https://linuxconfig.org/how-to-manage-acls-on-linux

gives the following result on my system, showing that the filesystem on /dev/sda3 has, among the default mount options, also ‘acl’.
If your filesystem has not been mounted with the ‘acl’ option, you can re-mount it giving the needed option:
Another thing we need, is to install the

As you can see, since we didn’t set any ACL permission on the file, the command just displays the standard permissions values, plus the file owner and the group owner, both having read and write permissions. Now let’s imagine we want to give a specific user (I will create this user on purpose and call him
We have three ‘sections’ divided by colons: in the first one, the
Finally, the name of the file on which we want to apply the permissions.
If we now try to run the ‘getfacl’ command, we can see that its output reflects the changes we made:
An entry has been added for the
In this case, only reading and writing permissions could be assigned with setfacl command. Of course we can change this option, using

As you can see, not only the changes we made to the mask is now reported, but also the effective permissions for the group owner and the named user
Other than explicitly changed with the command above, the ACLs mask also gets automatically re-calculated when we assign or change permissions with setfacl (unless the -n option is specified). Let’s demonstrate that: we will change the permissions of the

As you can see the mask got re-calculated and it now reflects the maximum permissions present for the named user
You can also use ACL to completely deny access to a file for a specific named user or group. For example, by running:

The

As expected, the file has been created automatically receiving the ACLs permissions specified above.
When you want to erase all the ACLs set, you can always run the setfacl with the
This tutorial covers the main aspects of ACLs, and of course there is a lot more about them to know, so I suggest, as always, to read the manual for a more in-deep knowledge. By now just remember that if you want to remove all the ACLs permissions assigned to a file, you just have to run
Objective
Introduction to the management of ACLs ( Access Control List ) on LinuxOperating System and Software Versions
- Operating System: - Linux distribution agnostic
Requirements
- Root access on a working Linux installation
- Knowledge of Discretionary permission system
- A filesystem which supports ACLs (e.g xfs, ext2, ext3, ext4), mounted with the ‘acl’ option
- Having the ‘acl’ package installed
Difficulty
MEDIUMConventions
- # - requires given command to be executed with root privileges either directly as a root user or by use of
sudocommand - $ - given command to be executed as a regular non-privileged user
Introduction
In this tutorial we will see what ACLs are, and how to do the basic manipulation of this kind of permissions on a Linux platform. The below instructions will work on any Linux distribution. I‘m assuming you know and are comfortable using standard Linux discretionary ugo/rwx permissions.So, what are ACLs ?
ACLs are a second level of discretionary permissions, that may override the standard ugo/rwx ones. When used correctly they can grant you a better granularity in setting access to a file or a directory, for example by giving or denying access to a specific user that is neither the file owner, nor in the group owner.Getting started
The first thing you have to do, if you want to take advantage of ACLs is to make sure that the filesystem you want to use them on, has been mounted with the ‘acl’ option. To verify the latter you can run the ‘tune2fs -l’ command, passing the partition as argument. As you can see running (output truncated):# tune2fs -l /dev/sda3

gives the following result on my system, showing that the filesystem on /dev/sda3 has, among the default mount options, also ‘acl’.
If your filesystem has not been mounted with the ‘acl’ option, you can re-mount it giving the needed option:
# mount -o remount -o acl /dev/sda1However, notice that the mount options set this way, will not be persistent, and will not survive a reboot. If you want to obtain persistence, you have to modify the filesystem mount options in /etc/fstab, assigning the ‘acl’ option statically.
Another thing we need, is to install the
acl package. This package contains various ACLs utilities like the getfacl and setfacl programs. A test case
Let’s see what ACLs can do for us. First we will create a file named text.cfg and we will give it as an argument to thegetfacl command. Let’s see what the output of this command shows: $ touch text.cfg && getfacl text.cfg

As you can see, since we didn’t set any ACL permission on the file, the command just displays the standard permissions values, plus the file owner and the group owner, both having read and write permissions. Now let’s imagine we want to give a specific user (I will create this user on purpose and call him
dummy ), a specific set of privileges on the file. We will just have to run: $ setfacl -m u:dummy:rw text.cfgLet’s analyze the command: first we have, of course, the name of the program
setfacl, which is pretty self-explanatory, than we passed the -m option (short for --modify) which allows us to change the ACLs of a file, than the permission descriptions u:dummy:rw. We have three ‘sections’ divided by colons: in the first one, the
u stands for user, specifying that we want to set the ACLs for a specific user. It could have been a g for group, or an o for others.
In the second section we have the name of the user whom we want to set
the permissions for, and in the third, the permissions to assign. Finally, the name of the file on which we want to apply the permissions.
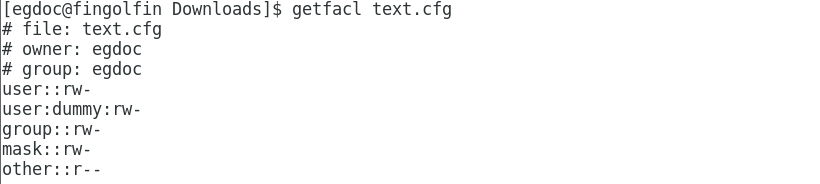
If we now try to run the ‘getfacl’ command, we can see that its output reflects the changes we made:
$ getfacl text.cfg

An entry has been added for the
dummy user, showing the permissions we assigned to him. Other than that, if you notice, also an entry for mask
has appeared. What does it stand for ? The mask associated with an ACL
limits the set of permissions that can be assigned on the file for the
the named groups and users and for the group owner, but has no effect on
the permissions for the file owner and the other permission group. In this case, only reading and writing permissions could be assigned with setfacl command. Of course we can change this option, using
setfacl program itself: $ setfacl -m mask:r text.cfgWith the command above, we set the mask to allow only reading permissions. Let’s check the output of
getfacl now: $ getfacl text.cfg

As you can see, not only the changes we made to the mask is now reported, but also the effective permissions for the group owner and the named user
dummy are showed. Although the group owner and the dummy
user have reading and writing permissions on the file, by changing the
mask, we have effectively limited their permissions to read only. As the
output of the command shows, they now are only allowed to read the
file. Other than explicitly changed with the command above, the ACLs mask also gets automatically re-calculated when we assign or change permissions with setfacl (unless the -n option is specified). Let’s demonstrate that: we will change the permissions of the
dummy user to rwx and then check the getfacl output: $ setfacl -m u:dummy:rwx text.cfg && getfacl text.cfg

As you can see the mask got re-calculated and it now reflects the maximum permissions present for the named user
dummy. Obviously, since now no previously set permissions are higher than the mask, there is no need for showing the #effective permission status. You can also use ACL to completely deny access to a file for a specific named user or group. For example, by running:
$ setfacl -m u:dummy:- text.cfgwe effectively deny all privileges to the
dummy user on the text.cfg file. Default ACLs
Thedefault
ACL is a specific type of permission assigned to a directory, that
doesn’t change the permissions of the directory itself, but makes so
that specified ACLs are set by default on all the files created inside
of it. Let’s demonstrate it: first we are going to create a directory
and assign default ACL to it by using the -d option: $ mkdir test && setfacl -d -m u:dummy:rw testnow, we can examine the output of the getfacl for that directory:
$ getfacl test

The
default
permissions has been assigned correctly. Now we can verify them by
creating a file inside of the test directory and checking its
permissions by running getfacl: $ touch test/file.cfg && getfacl test/file.cfg

As expected, the file has been created automatically receiving the ACLs permissions specified above.
When you want to erase all the ACLs set, you can always run the setfacl with the
-b option. This tutorial covers the main aspects of ACLs, and of course there is a lot more about them to know, so I suggest, as always, to read the manual for a more in-deep knowledge. By now just remember that if you want to remove all the ACLs permissions assigned to a file, you just have to run
setfacl with the -b (short for --remove-all) option. 
No comments:
Post a Comment