https://thebestvpn.com/public-wifi-security
Ever felt uneasy doing your online banking in your favorite coffee shop?
Me too.
Are you sure you want to hit “buy” on that chic blue and black (or was it gold and white?) dress, exposing your credit card details to cyber criminals who may be watching?
Think again.
I don’t blame you if every time you log onto social media, on public Wi-Fi, you worry if some hacker is about to steal your password.
My friend, you’re not alone.

Risk Based Security reports that in 2016 alone, there have been more than 4,100 security breaches totaling 4.2 billion stolen and exposed personal records – emails, passwords, SSNs, addresses etc.
Over 4 billion people at risk of identity theft, drained bank accounts or worse!
There are many tricks to ensure this never happens to you when using Public Wi-Fi. Best of all, we are going to show you all of them.
Feeling strongly about ensuring your safety, we decided to write this comprehensive article on public Wi-Fi security and show you step by step, how you can thwart hacking attempts on your systems.
Follow our step-by-step guide to a T and take a look at our exhaustive list of additional security strategies. Implement those which you think you can benefit from and your devices will become impenetrable fortresses.
In times where 87 percent of the population is using public networks and free Wi-Fi services, it is an imperative to practice good internet hygiene and ensure every precaution to secure one’s personal data, has been taken.
Fortunately for me and you, there are some awesome people out there which have made it their mission in life to simplify cybersecurity. Whether you’re a 16-year-old programming genius, a flashy management consultant or a single mom – we’ve got you covered.
Everything you will read below is straightforward and simple to implement.
Let me help you by giving you the necessary knowledge & tools to protect yourself from any and all cyber attackers every time you decide to click “connect” on an open Wi-Fi network.
Ready?
In this first part of our article I will be guiding you through the three most important steps you need to take to ensure maximum protection in the quickest time possible. These security precautions will take you only minutes to enforce and will make you practically invisible to hackers.
Really, kudos to you for giving a second thought to just how vulnerable you may be while waiting for your flight in that crowded airport.
The first thing you have to accept is that, like it or not, you’re exposing yourself to unnecessary dangers. Prevention is the best cure. Use public Wi-Fi only if you have implemented our next two steps.
Before I get to them, let’s explore how awareness can help you out.
Just like anything in life, being aware and mindful of your surroundings is of utmost importance. An often overlooked part of public Wi-Fi security is that first word – public.
Just because you’re connected to an open network, doesn’t mean all attacks will be carried over online.
Be mindful of who is peaking at your screen and never leave your technology unattended. Hackers can plug in a flash drive, which automatically installs malware, in half the time it takes you to grab your Latte from the cute barista.
Public Wi-Fi networks are inherently dangerous and incredibly attractive to no-gooders. The ability to blend in and potentially have physical access to their victim’s machines is too sweet to give up.
Do not, under any circumstance, provide access to your notebook to strangers. Never let anybody you don’t know touch your laptop. It’s your property and nobody has the right to touch it without a warrant!
Further, be proactive in your security habits. If you’re connecting to an unknown open Wi-Fi that asks you to download a client in order to connect, move on. Why risk it when you can connect without hassle to the another network two blocks down the road?
Sure, most of the time that client is just a method for your network provider to serve you pesky ads. A hacker, however, needs to trick you only once to download his fake client for you to get into deep trouble. More on this later.
If you practice habits of mindfulness and proactive thinking, you will easily be able to recognize sketchy situations to beware of.
They can’t get to you, if you outsmart them at their own game.
By disabling this option, you will block anybody, connected to the same network, from snooping around your files.
On default, this is already taken care of if the network is marked as public. Sometimes, however, you may mis-click and leave yourself exposed.
Even If you follow all security techniques, if sharing is not disabled – it’s no good. You’re practically installing a state of the art home alarm system, but leaving your front door open.
Anybody could access your files; they don’t even have to be a hacker.
How long did this take you, a minute? You’ve just made sure that nobody will be able to access or see any of your files. While this will deter low effort intrusions, it will do little for concentrated attacks.
In order to truly protect yourself from hackers, you have to…

Also known as The Holy Grail of identity protection.
The #1 tool you want to own and implement. If I could sum up Wi-Fi security in one sentence it would be USE A VPN!
Not wanting to bore you with technical jargon, let me give you a quick rundown on the benefits of a VPN, how these networks function and why you should spend 15 minutes setting up yours.
VPN stands for Virtual Private Network. Living up to its name, it encrypts your information, keeping it private and 100% anonymous.
In the olden days (read a few decades ago), VPNs were exclusively used by fortune 500 companies. Encrypting data and thereby enabling anonymous communications across vast distances was a much sought after solution in the highly competitive world of business.
As the years went on, the advantages of VPNs quickly gained popularity with the outside world. From small businesses to individuals; folks quickly learned the value of remaining anonymous online.
Once the VPN client is installed and set up, it takes only a couple of clicks to connect and start browsing securely.
I promised no technical jargon so I will only touch on how a VPN works. Make sure to read through our in-depth article on how VPN encrypt your data, if you’d like a more detailed look.
In the simplest of terms, a VPN transmits your data packets via a protected tunnel protocol. This protocol is layered with security features which will immediately sever the connection if an intrusion is detected. If an intrusion is attempted, the VPN will immediately reconnect through a different route, staying one step ahead.
It’s a cat and mouse game with the mouse being able to teleport to a new city anytime it spots the cat. The best part – you decide where to teleport. You can mask your traffic and connect to any server that your VPN provider provides.
To find a VPN, use this VPN review chart.
Wait!
The first step when connecting to an open Wi-Fi is to verify you’re actually connecting to it. It is incredibly easy for hackers to set up a fake Wi-Fi hotspot resembling the original one. Distracted by the pretty girl, you can easily be fooled into connecting with “La Wie” instead of “La Vie”.
The last thing you want is to willingly connect to said hacker and give him access to your system on a silver platter.
If unsure, call back that waiter and verify the name of their Wi-Fi.
Cyber criminals will take whatever they can get, but they are especially interested in banking details, passwords and personal information.
Don’t ever log into your online banking service or Paypal. Delay your banking activities for when you’re at home.
It would be impossible to list all sites and activities you should avoid, here are the most important ones:
If you have to access such a file, opt for remote access to your home system instead. Just make sure it’s not residing in the laptop you’re using in public.
 A
less secure alternative is to hide all folders containing sensitive
information. On windows, just right click a folder and navigate to its Properties. In the Attributes tab, enable the “Hidden” option.
A
less secure alternative is to hide all folders containing sensitive
information. On windows, just right click a folder and navigate to its Properties. In the Attributes tab, enable the “Hidden” option.
To display hidden folders, go to your file explorer’s View tab and check Hidden Items in the Show/Hide pane on the far right side.
Websites which have set up a SSL are easily recognizable. You need only look at the address bar of your browser. Take a look at ours for example:
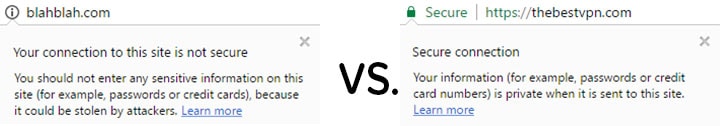
SSL certificates are neither cheap nor easy to procure. To be awarded an SSL certificate, a website owner must implement several security measures and answer a number of questions about the identity of their website and company.
Firewall is a standard software or hardware network security system built into most operating systems. Your firewall is data packet filter which monitors an incoming and outgoing traffic and connection attempts. It’s a warden which only permits trusted networks to communicate with you. Anything fishy will get blocked by your firewall.
Safe to say, we want this enabled. Here’s how to do it…
For the rest of you, keeping your Antivirus up to date is an imperative. The updates are of vital importance to detecting newly coded malware and staying one step ahead of cyber attacks. I promise you, if you’re to be unlucky and have your data compromised, a system restart will seem a small price to pay in hindsight.
A curious statistics is the percentage of people who do not make full use of their antivirus software. According to a 2015 report by OPSWAT, 91.3% of antivirus users hadn’t run a full full system scan via their installed antivirus product within the last seven days.
If I have to be honest with you, I am part of that 90+%. That said, if you’re often making use of public Wi-Fi hotspots, a full or quick scan of your system might be a good idea.
Having said that, not all browsers are created equal. Take a look at this 2016 vulnerabilities chart.
More important than keeping your browser up to date is making sure your system itself has been updated. Whether you’re running Windows, OS X, Android or iOS, checking your up to date status is a healthy habit you should cultivate.

 Though a bit cumbersome at times, Two Factor Authentication has saved me more than once.
Though a bit cumbersome at times, Two Factor Authentication has saved me more than once.
63 times to be precise. Since early 2015, someone has attempted to hack my Twitter 63 times (Yes, I counted)
Notice the time stamps, all codes sent at 9:58. Clearly a hacker.
I admire his or her persistence, the last hacking attempt was made just two days ago. Still, no cigar. Bless Two Factor Authentication!
Tell me if this sound familiar to you. You have two or three “main” passwords each with several variations. One site requires 8 character passwords, another requires numbers and special symbols and a third one wants less than 8 with no special symbols at all.
I do my forearm exercises at the gym and college tested my memory skills enough, thank you very much.
Now think if every password you had to use had to be a one, unique to that specific website. Two weeks ago I cleared my browser history, including my saved passwords.
Since then, my Chrome’s Password Auto-fill has saved passwords to 56 sites (Yeah, I counted again…). Now, I may be a bigger nerd than most people, still – 56 password protected sites. Imagine if you had to have a unique one to every one of these.
Saving your passwords to a notepad is the biggest no-go, since that is the first thing intruders will look for. On the flip side, if a hacker does get access to your password and it’s the same password you use everywhere, you are in BIG trouble.
Since we’re best friends, let me level with you; do I use a password manager? No.
Should I ? Yes, and so should you.
This is useful in emergency situations where you’re forced to engage in high-profile activities.
Keeping that in mind, I feel the need to note that any device connected to the internet could never be 100% unhackable and is potentiall susceptible to outside attacks.
At least if your mobile data gets hacked you have someone to blame, free iPhones anyone?
*Ba Dum Tss*
Dad jokes aside, turning off your Wi-Fi when not in use will block any and all attempt of tampering. It’s your ultimate defense. If you’re sitting in a train or airport, watching a movie, turn your Wi-Fi off.
Not only will you be safe from no-gooders you will also take advantage of the added benefit of power savings, prolonging your battery life.
Two birds with one stone? Don’t mind if I do.
You can take all the preventative measures in the world, but if you are forced to reset your laptop, reinstall your operating system or otherwise, you have to do it all over again. In these instances, making sure your system doesn’t connect prematurely, before you’ve repeated all security steps, is of utmost importance.
Select a network and click on Forget. This will ensure you will have to connect manually next time.
The primary purpose of a Wi-Fi client is the ability to meter your bandwidth usage. This is entirely useless unless you’re paying for your Wi-Fi, or if the hotspot provider wishes to limit your internet usage; blocking torrenting for example.
While this makes sense in a respected hotel chain or paid network you should be weary anytime this is required with a free network.
If you’re finding yourself in the Parisian Charles de Gaulle airport and you don’t wish to pay their exorbitant “20 min for €2.90″ fees for Wi-Fi, make sure to shop around. You’ll find nearby coffee shops with their own Wi-Fi.
Always make sure you’re choosing the best network. I would rather connect to a free network without installing a download client than an expensive “more secure” one.
Tor is also known as the “deep web” or the “dark web” as once you connect to it, you can browse to websites accessible only in the Tor network. These websites often have obscure, randomly generated domain names and can be distinguished with the .onion instead of a .com.
Here is the domain name of the anonymity search engine “DuckDuckGo”: http://3g2upl4pq6kufc4m.onion
There are several disadvantages to using Tor. First is the super long loading times. With your traffic having to be bounced by several servers, webpages take an eternity to load.
Tor was created in the conjunction with the U.S. Navy and many government agency use Tor. The network is widely used in countries with censorship laws; political refugees, journalists but also criminals.
Due to the anonymity of the network, many criminals have made it their safe haven. Drugs, guns, false identities and worse are sold on certain websites within the Tor network.
While government can’t track what you do on Tor, the network isn’t foolproof. Certain software vulnerabilities and website admin errors can and are exploited by government agency. In 2013, Tor’s biggest black market website – The Silk Road – was busted by the FBI.
In June 2014 the Cyber Security Research Institute conducted an experiment in some of the busiest neighborhoods in London. Backed by the European law enforcement agency Europol and sponsored by F-Secure, security researches set up a free Wi-Fi hotspot and tested just how attentive Londoners really are.
All you had to do to connect, was to accept a Terms of Service agreement. Buried in the fineprint, however, there was a clause which stated “the recipient agreed to assign their first born child to us for the duration of eternity.”
Six Londoners agreed.
This tongue-in-cheek experiment highlights the serious risks you willingly accept in order to connect to free Wi-Fi.
Nobody reads Terms of Service agreements, but you would be well-advised to skim them over and look for any irregularities. Terms of Services are legally binding, the last thing you want to do is to connect to a hacker’s public Wi-Fi network and agree to hand over sensitive data such as GPS locations or personal information.
Oh, and by the way, Finnish security firm F-Secure said it had decided not to enforce the clause. Phew!
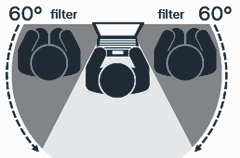 The first time I saw a privacy screen in action, the look on my face must have been awesome.
The first time I saw a privacy screen in action, the look on my face must have been awesome.
This guy in a suit was staring at a black screen and typing away. Little did I know, he was using a privacy filter which severely restricts viewing angles. The laptop screen is visible only when looked at dead on. Such filters are often used by bank tellers and installed in ATMs.
Procrastinating roommates, nosy coworkers or even fellow fliers – prying eyes are everywhere. Not only does it become annoying and uncomfortable to have your screen stared at, it’s downright dangerous in public environment where you can’t always know just who is looking over your shoulder.
I sincerely hope this article has helped you find your preferred method of keeping yourself safe on the inter-webs. Please share it with your friends and colleagues and let me know about your experiences with public Wi-Fi.
Surf Safe,
Andrey
Ever felt uneasy doing your online banking in your favorite coffee shop?
Me too.
Are you sure you want to hit “buy” on that chic blue and black (or was it gold and white?) dress, exposing your credit card details to cyber criminals who may be watching?
Think again.
I don’t blame you if every time you log onto social media, on public Wi-Fi, you worry if some hacker is about to steal your password.
My friend, you’re not alone.

(Source: Symantec Personal Breaches)
According
to leading cybersecurity firm Symantec (SYMC:NASDAQ), millions of
Americans who access their personal emails (58 percent), log into social
media platforms (56 percent) or do their online banking (22 percent) on
Public Wi-Fi networks, are opening themselves up to being spied on;
getting their passwords and credit card details stolen.Risk Based Security reports that in 2016 alone, there have been more than 4,100 security breaches totaling 4.2 billion stolen and exposed personal records – emails, passwords, SSNs, addresses etc.
Over 4 billion people at risk of identity theft, drained bank accounts or worse!
There are many tricks to ensure this never happens to you when using Public Wi-Fi. Best of all, we are going to show you all of them.
Feeling strongly about ensuring your safety, we decided to write this comprehensive article on public Wi-Fi security and show you step by step, how you can thwart hacking attempts on your systems.
Follow our step-by-step guide to a T and take a look at our exhaustive list of additional security strategies. Implement those which you think you can benefit from and your devices will become impenetrable fortresses.
In times where 87 percent of the population is using public networks and free Wi-Fi services, it is an imperative to practice good internet hygiene and ensure every precaution to secure one’s personal data, has been taken.
Fortunately for me and you, there are some awesome people out there which have made it their mission in life to simplify cybersecurity. Whether you’re a 16-year-old programming genius, a flashy management consultant or a single mom – we’ve got you covered.
Everything you will read below is straightforward and simple to implement.
Let me help you by giving you the necessary knowledge & tools to protect yourself from any and all cyber attackers every time you decide to click “connect” on an open Wi-Fi network.
Ready?
Step-By-Step Public Wi-Fi Security Guide
In this first part of our article I will be guiding you through the three most important steps you need to take to ensure maximum protection in the quickest time possible. These security precautions will take you only minutes to enforce and will make you practically invisible to hackers.

1. Be Mindful & Proactive
Congratulations! By reading these very lines you already completed step one to securing yourself from cyber attacks.Really, kudos to you for giving a second thought to just how vulnerable you may be while waiting for your flight in that crowded airport.
The first thing you have to accept is that, like it or not, you’re exposing yourself to unnecessary dangers. Prevention is the best cure. Use public Wi-Fi only if you have implemented our next two steps.
Before I get to them, let’s explore how awareness can help you out.
Just like anything in life, being aware and mindful of your surroundings is of utmost importance. An often overlooked part of public Wi-Fi security is that first word – public.
Just because you’re connected to an open network, doesn’t mean all attacks will be carried over online.
Be mindful of who is peaking at your screen and never leave your technology unattended. Hackers can plug in a flash drive, which automatically installs malware, in half the time it takes you to grab your Latte from the cute barista.
Public Wi-Fi networks are inherently dangerous and incredibly attractive to no-gooders. The ability to blend in and potentially have physical access to their victim’s machines is too sweet to give up.
Do not, under any circumstance, provide access to your notebook to strangers. Never let anybody you don’t know touch your laptop. It’s your property and nobody has the right to touch it without a warrant!
Further, be proactive in your security habits. If you’re connecting to an unknown open Wi-Fi that asks you to download a client in order to connect, move on. Why risk it when you can connect without hassle to the another network two blocks down the road?
Sure, most of the time that client is just a method for your network provider to serve you pesky ads. A hacker, however, needs to trick you only once to download his fake client for you to get into deep trouble. More on this later.
If you practice habits of mindfulness and proactive thinking, you will easily be able to recognize sketchy situations to beware of.
They can’t get to you, if you outsmart them at their own game.
2. Turn OFF “Sharing”
Moving onto a more practical and critical step of network security – turning off sharing.By disabling this option, you will block anybody, connected to the same network, from snooping around your files.
On default, this is already taken care of if the network is marked as public. Sometimes, however, you may mis-click and leave yourself exposed.
Even If you follow all security techniques, if sharing is not disabled – it’s no good. You’re practically installing a state of the art home alarm system, but leaving your front door open.
Anybody could access your files; they don’t even have to be a hacker.
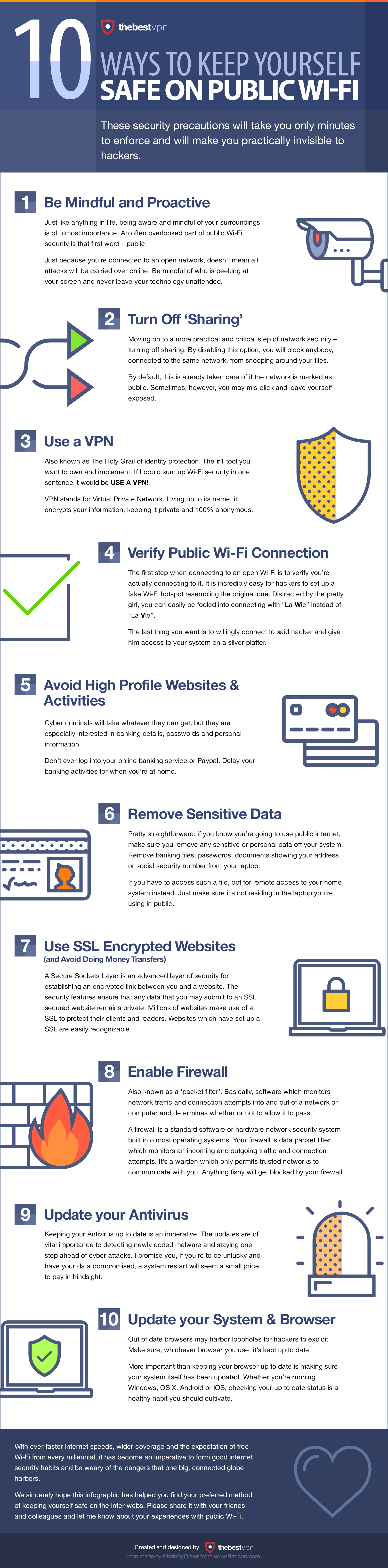
How to Turn Off Sharing on Windows
- Open your control panel and click on Network and Internet.
- Click through to Network and Sharing centre.
- Find Change advanced sharing settings and click it.
- There are two main options you want to disable: Network discovery & File and printer sharing. Turn both of these off.
P.S. Make sure you do this both for “Private” and “Guest or Public” networks!

How to Turn Off Sharing on Mac (OS X)
- Navigate to “System Preferences”.
- Under “Internet & Wireless” click on the “Sharing” folder icon.
- Find the list of sharing options on the left hand site of the new screen. T
- To disable sharing, simply uncheck the options named “File Sharing”.
How long did this take you, a minute? You’ve just made sure that nobody will be able to access or see any of your files. While this will deter low effort intrusions, it will do little for concentrated attacks.
In order to truly protect yourself from hackers, you have to…
3. Use a VPN

Also known as The Holy Grail of identity protection.
The #1 tool you want to own and implement. If I could sum up Wi-Fi security in one sentence it would be USE A VPN!
Not wanting to bore you with technical jargon, let me give you a quick rundown on the benefits of a VPN, how these networks function and why you should spend 15 minutes setting up yours.
VPN stands for Virtual Private Network. Living up to its name, it encrypts your information, keeping it private and 100% anonymous.
In the olden days (read a few decades ago), VPNs were exclusively used by fortune 500 companies. Encrypting data and thereby enabling anonymous communications across vast distances was a much sought after solution in the highly competitive world of business.
As the years went on, the advantages of VPNs quickly gained popularity with the outside world. From small businesses to individuals; folks quickly learned the value of remaining anonymous online.
Once the VPN client is installed and set up, it takes only a couple of clicks to connect and start browsing securely.
I promised no technical jargon so I will only touch on how a VPN works. Make sure to read through our in-depth article on how VPN encrypt your data, if you’d like a more detailed look.
In the simplest of terms, a VPN transmits your data packets via a protected tunnel protocol. This protocol is layered with security features which will immediately sever the connection if an intrusion is detected. If an intrusion is attempted, the VPN will immediately reconnect through a different route, staying one step ahead.
It’s a cat and mouse game with the mouse being able to teleport to a new city anytime it spots the cat. The best part – you decide where to teleport. You can mask your traffic and connect to any server that your VPN provider provides.
To find a VPN, use this VPN review chart.
4. Verify Public Wi-Fi Connection
It’s a beautiful, sunny day and you sit down in the newly opened french bistro around the corner; “La Vie” (I’m terrible at coming up with fake bistro names). You ask your waiter for the Wi-Fi password as you notice the pretty girl sitting a few feet from you…Wait!
The first step when connecting to an open Wi-Fi is to verify you’re actually connecting to it. It is incredibly easy for hackers to set up a fake Wi-Fi hotspot resembling the original one. Distracted by the pretty girl, you can easily be fooled into connecting with “La Wie” instead of “La Vie”.
The last thing you want is to willingly connect to said hacker and give him access to your system on a silver platter.
If unsure, call back that waiter and verify the name of their Wi-Fi.
5. Avoid High Profile Websites & Activities
Listen, you’ve been owing aunt Sue those $20 for months; she can wait a few more hours.Cyber criminals will take whatever they can get, but they are especially interested in banking details, passwords and personal information.
Don’t ever log into your online banking service or Paypal. Delay your banking activities for when you’re at home.
It would be impossible to list all sites and activities you should avoid, here are the most important ones:
- Online banking & Financial Services
- Emails
- Social Media
- Utilities
- …and anything that will have you typing in sensitive information – SSN, Address etc
6. Remove Sensitive Data
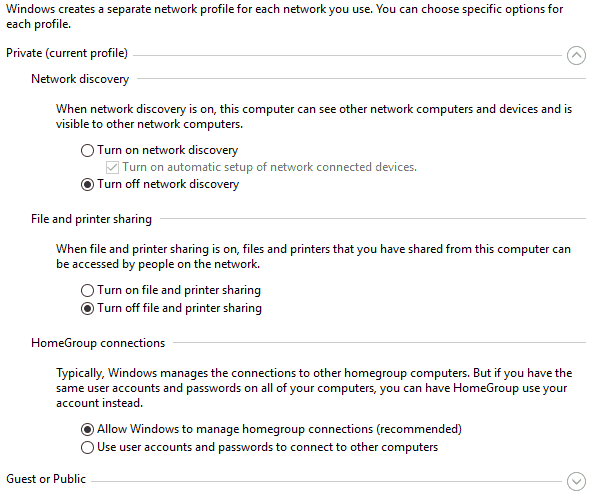
Pretty straightforward, if you know you’re going to use public internet, make sure you remove any sensitive or personal data off your system. Remove banking files, passwords, documents showing your address or social security number from your laptop.If you have to access such a file, opt for remote access to your home system instead. Just make sure it’s not residing in the laptop you’re using in public.
 A
less secure alternative is to hide all folders containing sensitive
information. On windows, just right click a folder and navigate to its Properties. In the Attributes tab, enable the “Hidden” option.
A
less secure alternative is to hide all folders containing sensitive
information. On windows, just right click a folder and navigate to its Properties. In the Attributes tab, enable the “Hidden” option.To display hidden folders, go to your file explorer’s View tab and check Hidden Items in the Show/Hide pane on the far right side.

7. Use SSL Encrypted Websites (and Avoid Doing Money Transfers)
A Secure Sockets Layer is an advanced layer of security for establishing an encrypted link between a you and a website. The security features ensure that any data that you may submit to an SSL secured website remains private. Million of websites make use of a SSL to protect their clients and readers.Websites which have set up a SSL are easily recognizable. You need only look at the address bar of your browser. Take a look at ours for example:

SSL certificates are neither cheap nor easy to procure. To be awarded an SSL certificate, a website owner must implement several security measures and answer a number of questions about the identity of their website and company.
8. Enable Firewall
Also known as a ‘packet filter’. Basically, software which monitors network traffic and connection attempts into and out of a network or computer and determines whether or not to allow it to pass. Depending on the sophistication, this can be limited to simple IP/port combinations or do full content-aware scans.Firewall is a standard software or hardware network security system built into most operating systems. Your firewall is data packet filter which monitors an incoming and outgoing traffic and connection attempts. It’s a warden which only permits trusted networks to communicate with you. Anything fishy will get blocked by your firewall.
Safe to say, we want this enabled. Here’s how to do it…
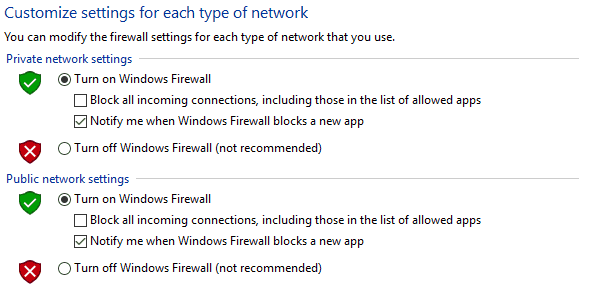
How to Disable Firewall on Windows
- Open your Control Panel and click on System and Security.
- Navigate to your Windows Firewall.
- Check out the left panel and click on “Turn Windows Firewall on or off“.
Pretty straightforward from there. This is how it should look:

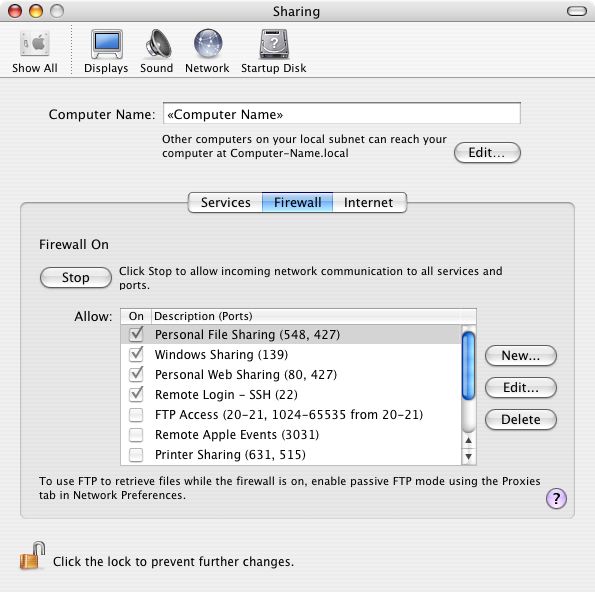
How to Disable Firewall on MacBook
Apple’s
Firewall works differently since their OS X v10.5.1 update. They
operate on a per-application basis. Often programs and
services are flagged by your Firewall as a false positive. With OS X you
can configure your Firewall to allow traffic from these programs and
services.
To enable your Firewall on your OS X system follow these steps:
- Choose System Preferences from your Apple menu and click on Security or Security & Privacy.
- Navigate to the Firewall tab and unlock the pane by clicking the lock in the lower-left corner and enter the administrator username and password.
- Click on “Turn On Firewall” or “Start“.

To further customize your firewall and enable specific apps and services to circumvent your firewall, click Advanced.
9. Update your Antivirus
If you’re part of the 84.9% of antivirus users with updated software; kudos to you.For the rest of you, keeping your Antivirus up to date is an imperative. The updates are of vital importance to detecting newly coded malware and staying one step ahead of cyber attacks. I promise you, if you’re to be unlucky and have your data compromised, a system restart will seem a small price to pay in hindsight.
A curious statistics is the percentage of people who do not make full use of their antivirus software. According to a 2015 report by OPSWAT, 91.3% of antivirus users hadn’t run a full full system scan via their installed antivirus product within the last seven days.
If I have to be honest with you, I am part of that 90+%. That said, if you’re often making use of public Wi-Fi hotspots, a full or quick scan of your system might be a good idea.
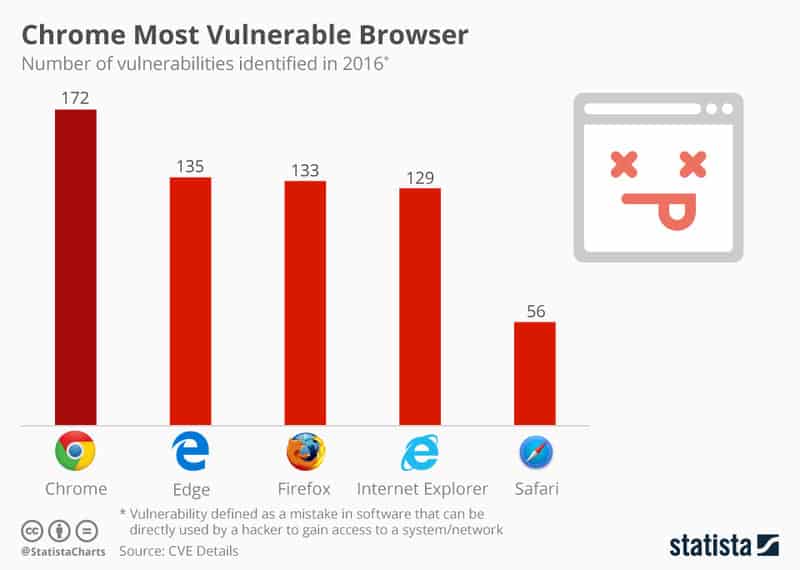
10. Update your System & Browser
Out of date browsers may harbor loopholes for hackers to exploit. Make sure, whichever browser you use, it’s kept up to date.Having said that, not all browsers are created equal. Take a look at this 2016 vulnerabilities chart.

More important than keeping your browser up to date is making sure your system itself has been updated. Whether you’re running Windows, OS X, Android or iOS, checking your up to date status is a healthy habit you should cultivate.
11. Implement Two Factor Authentication
Two Factor Authentication is a genius way to ensure you and only you can access websites or services which require a password.
(Source: Two Factor Authentication – What is it?)
A Two
Factor Authentication system connects your account to your phone
number. Any login attempt will automatically prompt an authentication
code to be sent to your phone by text messages (free of charge) which
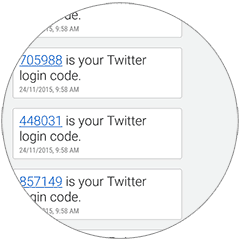
you will then have to type in next to your password in order to log in. Though a bit cumbersome at times, Two Factor Authentication has saved me more than once.
Though a bit cumbersome at times, Two Factor Authentication has saved me more than once.63 times to be precise. Since early 2015, someone has attempted to hack my Twitter 63 times (Yes, I counted)
Notice the time stamps, all codes sent at 9:58. Clearly a hacker.
I admire his or her persistence, the last hacking attempt was made just two days ago. Still, no cigar. Bless Two Factor Authentication!
12. Keep Passwords Unique
One of the biggest self-imposed vulnerabilities is using the same password for every service, account and website we use. Once this password leaks, everything we fight hard to protectTell me if this sound familiar to you. You have two or three “main” passwords each with several variations. One site requires 8 character passwords, another requires numbers and special symbols and a third one wants less than 8 with no special symbols at all.
I do my forearm exercises at the gym and college tested my memory skills enough, thank you very much.
Now think if every password you had to use had to be a one, unique to that specific website. Two weeks ago I cleared my browser history, including my saved passwords.
Since then, my Chrome’s Password Auto-fill has saved passwords to 56 sites (Yeah, I counted again…). Now, I may be a bigger nerd than most people, still – 56 password protected sites. Imagine if you had to have a unique one to every one of these.
Saving your passwords to a notepad is the biggest no-go, since that is the first thing intruders will look for. On the flip side, if a hacker does get access to your password and it’s the same password you use everywhere, you are in BIG trouble.

(Source: Keeper)
The
solution to this problem is a secure Password Manager. A password
managers will create high-strength, random passwords, store them
securely and auto-fill them. Across any and all devices.Since we’re best friends, let me level with you; do I use a password manager? No.
Should I ? Yes, and so should you.
13. Use Mobile Data Instead
While your cell phone isn’t hack-proof, hackers who are targeting open networks won’t be able to hijack your mobile data.This is useful in emergency situations where you’re forced to engage in high-profile activities.
Keeping that in mind, I feel the need to note that any device connected to the internet could never be 100% unhackable and is potentiall susceptible to outside attacks.
At least if your mobile data gets hacked you have someone to blame, free iPhones anyone?
14. Turn Off Wi-Fi When Not in Use
I have to admit something – I lied. There is one thing that trumps VPNs – turning of your Wi-Fi*Ba Dum Tss*
Dad jokes aside, turning off your Wi-Fi when not in use will block any and all attempt of tampering. It’s your ultimate defense. If you’re sitting in a train or airport, watching a movie, turn your Wi-Fi off.
Not only will you be safe from no-gooders you will also take advantage of the added benefit of power savings, prolonging your battery life.
Two birds with one stone? Don’t mind if I do.
15. “Forget” Public Networks
As a rule of thumb you will want to disable auto-connect and delete public Wf-Fi networks once you’re done with them.You can take all the preventative measures in the world, but if you are forced to reset your laptop, reinstall your operating system or otherwise, you have to do it all over again. In these instances, making sure your system doesn’t connect prematurely, before you’ve repeated all security steps, is of utmost importance.
How to “Forget” Public Networks on Windows
- Open your Control panel and click on Network and Internet.
- Click through to Network and Sharing center.
- In the left pannel, click on Change adapter settings.
- In the new window, double click on your Wi-Fi connection. Another window will open.
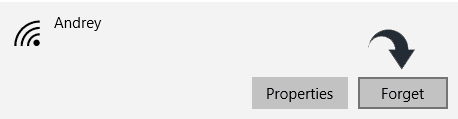
- Click on the fourth option; Manage known networks.
Select a network and click on Forget. This will ensure you will have to connect manually next time.

How to “Forget” Networks on MacBook
- Click on the Wi-Fi symbol on the top menu bar and
- Then, click on Open Network Preferences at the bottom of the drop down menu.
- Click on Wi-Fi in the menu on the left and click Advanced at the bottom right of the new window.
- Select the WiFi network you want to forget, and click the minus sign.
16. Don’t Install Connection Clients
Unless you’re staying at a hotel or an otherwise trusted Wi-Fi provider, downloading and installing a client in order to connect to a free Wi-Fi network is both unnecessary and fishy.The primary purpose of a Wi-Fi client is the ability to meter your bandwidth usage. This is entirely useless unless you’re paying for your Wi-Fi, or if the hotspot provider wishes to limit your internet usage; blocking torrenting for example.
While this makes sense in a respected hotel chain or paid network you should be weary anytime this is required with a free network.
17. Find Best Network
Piggy bagging from #13, you want to make sure you’re choosing the best network to connect to. Paid is not always better than free, and free can often be twice as cumbersome as paid.If you’re finding yourself in the Parisian Charles de Gaulle airport and you don’t wish to pay their exorbitant “20 min for €2.90″ fees for Wi-Fi, make sure to shop around. You’ll find nearby coffee shops with their own Wi-Fi.
Always make sure you’re choosing the best network. I would rather connect to a free network without installing a download client than an expensive “more secure” one.
18. Use TOR
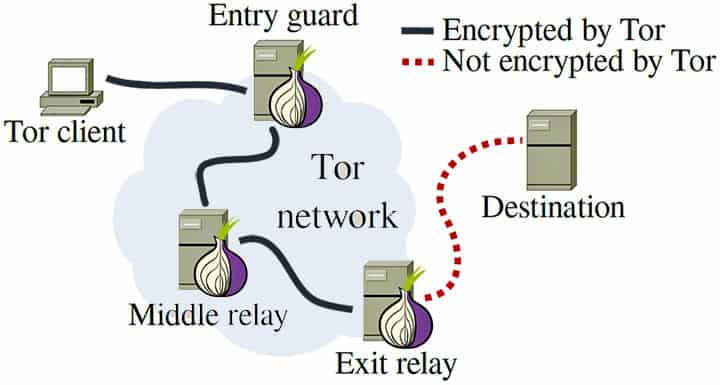
Tor is a free software which enables you to browse anonymously via a volunteer-operated networks of servers. Named after the original project “The Onion Router”, Tor relays your data through several points before sending it to your destination. This effectively conceals your location and negates any surveillance or tracking or tracing efforts.
Tor is also known as the “deep web” or the “dark web” as once you connect to it, you can browse to websites accessible only in the Tor network. These websites often have obscure, randomly generated domain names and can be distinguished with the .onion instead of a .com.
Here is the domain name of the anonymity search engine “DuckDuckGo”: http://3g2upl4pq6kufc4m.onion
There are several disadvantages to using Tor. First is the super long loading times. With your traffic having to be bounced by several servers, webpages take an eternity to load.
Tor was created in the conjunction with the U.S. Navy and many government agency use Tor. The network is widely used in countries with censorship laws; political refugees, journalists but also criminals.
Due to the anonymity of the network, many criminals have made it their safe haven. Drugs, guns, false identities and worse are sold on certain websites within the Tor network.
While government can’t track what you do on Tor, the network isn’t foolproof. Certain software vulnerabilities and website admin errors can and are exploited by government agency. In 2013, Tor’s biggest black market website – The Silk Road – was busted by the FBI.
19. Read Free Wi-Fi TOC
I can hear your sigh, but stay with me. You’ll want to read this.In June 2014 the Cyber Security Research Institute conducted an experiment in some of the busiest neighborhoods in London. Backed by the European law enforcement agency Europol and sponsored by F-Secure, security researches set up a free Wi-Fi hotspot and tested just how attentive Londoners really are.
All you had to do to connect, was to accept a Terms of Service agreement. Buried in the fineprint, however, there was a clause which stated “the recipient agreed to assign their first born child to us for the duration of eternity.”
Six Londoners agreed.
This tongue-in-cheek experiment highlights the serious risks you willingly accept in order to connect to free Wi-Fi.
Nobody reads Terms of Service agreements, but you would be well-advised to skim them over and look for any irregularities. Terms of Services are legally binding, the last thing you want to do is to connect to a hacker’s public Wi-Fi network and agree to hand over sensitive data such as GPS locations or personal information.
Oh, and by the way, Finnish security firm F-Secure said it had decided not to enforce the clause. Phew!
20. Buy a Privacy Screen/Filter
 The first time I saw a privacy screen in action, the look on my face must have been awesome.
The first time I saw a privacy screen in action, the look on my face must have been awesome.This guy in a suit was staring at a black screen and typing away. Little did I know, he was using a privacy filter which severely restricts viewing angles. The laptop screen is visible only when looked at dead on. Such filters are often used by bank tellers and installed in ATMs.
Procrastinating roommates, nosy coworkers or even fellow fliers – prying eyes are everywhere. Not only does it become annoying and uncomfortable to have your screen stared at, it’s downright dangerous in public environment where you can’t always know just who is looking over your shoulder.
Conclusion
With ever faster internet speeds, wider coverage and the expectation of free Wi-Fi from every millennial, it has become an imperative to form good internet security habits and be weary of the dangers that one big, connected globe harbors.I sincerely hope this article has helped you find your preferred method of keeping yourself safe on the inter-webs. Please share it with your friends and colleagues and let me know about your experiences with public Wi-Fi.
Surf Safe,
Andrey

No comments:
Post a Comment